Connecting with Secure Shell
Secure shell (SSH) is used to connect to command line sessions on remote systems using a secure (encrypted) connection.
If you wish to verify the server's authenticity before connecting, the timesharing server's SSH key fingerprint is shown below:
SHA256:/Y4i041azse1Yj4Edo8xnnz4AVijVdvsXN4H0UKy6mg.
How to connect
Register for access
First, ensure that you have registered for a Unix account. This only needs to be done once.
Activate the 24hr login pass
Before connecting to the system you need to log into the NUIT Application Access Portal and from the "Roles" tab, select "NUIT Unix Service" from the dropdown list:
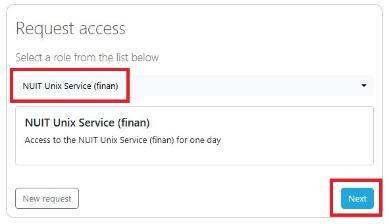
Choose Next and on the next page either leave the default 24hr time period or set your own and click "Next" to activate the login role.
Connect with your SSH client
Now, connect with your SSH client using the following details:
- Server Name: unix.ncl.ac.uk
- Username: (your University login ID with no "campus" or "newcastle.ac.uk" parts)
- Password: (your University login password)
Troubleshooting Tips
- If your connection is refused, please wait for a minute or so and try again. Sometimes the login role may take up to 30 seconds to activate.
